Operating a hotel in China, both in terms of daily operational of the hotel and group-level sales and marketing business, requires heavy data use and, for international hotels, cross-border data transfer (“CBDT”) of personal information (“PI”). Such CBDT has been the subject of somewhat onerous Chinese regulations. However, a new rule, known as Provisions on Facilitating and Standardizing Cross-Border Flow of Data, released by the Cyberspace Administration of China (“CAC”) on March 22, 2024 and which went into effect the same day (the “New Rule”) should have the effect of simplifying what is required of international hotels. However, the New Rule is still strict, and there are penalties for those who don’t comply.
In this write-up, we provide: (i) a summary of China’s CBDT Mechanisms as revamped by the New Rule; (ii) which hotel business scenarios are subject to CBDT reviews; (iii) how best to deal with law enforcement, where required; and (iv) other FAQs.
China’s CBDT Mechanisms
At a high level, in the post-New Rule era, China’s CBDT mechanism as it relates to PI can be summarized as follows: the regulatory framework classifies and grades the risk of CBDT based on the PI export volume. Broadly speaking, the larger the volume, the higher the risk level and the stricter the control measures; conversely, the smaller the PI transfer volume, the lessor the risk and more relaxed control measures apply. For CBDT where the PI involved reaches a threshold volume, one of three transfer mechanisms will apply: security assessment; standard contract filing or security certification (the “Transfer Mechanisms”), which are overseen by CAC.
- Security Assessment
Large-scale CBDT, i.e. transfer of more than one million individuals’ personal data or more than 10,000 individuals’ sensitive personal data from January 1st of the current calendar year (“YTD Period”), will require security assessment. Security assessment is a two-step process, where a provincial CAC will first complete a preliminary formality review and forward the application to the central CAC in Beijing for the final substantive review.
- Standard Contract Filing and Security Certification
For medium-scale CBDT, i.e. transfer of more than 100,000 individua’s personal data or more than one individual’s sensitive personal data in a YTD Period this will require standard contract filing or security certification. Standard contract filing and security certification are overseen by provincial CAC only – the application doesn’t have to go to central CAC in Beijing for final approval and is considered simpler and more straightforward than the security assessment.
It should be noted that international hotel groups are all likely to have to follow Security Assessment as their applicable Transfer Mechanism. Since guests’ accommodation information and identification documents are considered sensitive PI, almost all international hotel groups will meet the threshold volume for security assessment. Assuming a 200-key property with a 70% occupancy, assuming de-duplication resulting from repeated booking is offset against increments from co-staying guests, total tally of individuals in a calendar year will be more than 50,000 (200*0.7*365=51,100). That said, it might take less than three months for a single property to hit the 10,000-volume threshold for security assessment.
On a consolidated basis, it’s safe to say that an international hotel group with one sizeable property successfully operating in China will almost always meet the volume threshold for security assessment.
Hotel business scenarios subject to CBDT reviews
International hotel groups operating in China generally adopt two business models: management or franchise. Under the management model, the hotel group provides the brand, system, and management expertise to the hotel owner. In the franchise model, the hotel group provides just the brand and systems to the hotel owner.
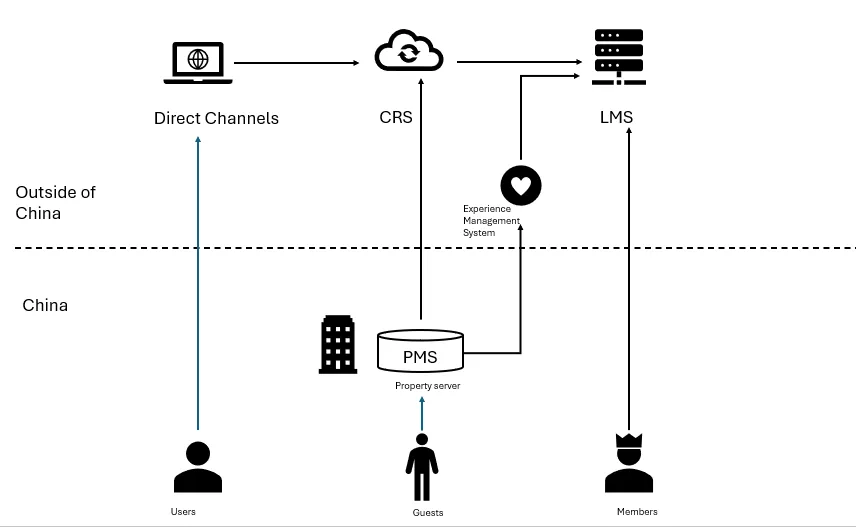
In each case, the licensed systems would include three core electronic systems for hotel booking, operation, and experience management: the Central Reservation System (CRS), Property Management System (PMS), and Loyalty Program Management System (LMS). Ancillary to these core systems, the licensed systems may also include an experience management system, payment system (POS), revenue management system, customer service system, and experience survey system, among other data management systems.
Of these core systems, except for the PMS, which is generally deployed on the property by a local server or on local clouds in China, the CRS and LMS systems are almost always deployed overseas.
The core systems process data for most, if not all, topline business scenarios, including:
- Reservations
When it comes to reservations, the booking “channels” collect information such as a guest’s name, payment card information, planned travel time, booked hotel name, and contact information to complete a booking. The data link transfers from the guest’s booking channel (a deemed in-China channel) to the CRS (an overseas data center), and after the CRS creates an order, it dispatches the order, along with the guest’s personal data, to a hotel’s PMS to block inventory. Booking channels are complex and can be divided into online channels (such as websites) and offline channels (such as walk-in booking at front desk), as well as direct channels and third-party OTA channels, and can also be divided into retail channels and distribution channels. However, as long as the channel is located in China, it will involve CBDT. Hotel websites and mobile apps, even if deployed outside of China, will be deemed as in-China channels if they are in Chinese language and targeting Chinese users to collect data.
- Loyalty member management
Functionalities in a loyalty member management scenario include enrollment, account management, earn-and-burn, point exchange, etc.
For enrollment and account management, there is a high degree of overlapping between the loyalty channel and reservation channel, as well as data links. The data being collected include member name, payment card information, home address, contact information, point changes, etc. Similar to reservations, since the LMS is deployed overseas, the process involves CBDT.
- Management of guest experience
During a guest’s hotel stay, the hotel often collects their service requests and preferences, summarizes them, and transmits them from PMS or other on-property terminals to an experience management system deployed overseas. The guest experience management system records such PI in the guest’s membership profile in the member database. This process involves CBDT.
In addition to these topline scenarios, backstage applications including job candidate application, individual contact information for B2B CRM scenarios (vendor/supplier management, MICE clients) which are also subject to review as part of the security assessment process. HR management is exempted from review.
Most international hotel groups operating in China are already in the process of completing a security assessment for both their topline business scenarios and backstage business enarios. To save costs, these hotel groups usually report their CBDT on behalf of all of its participating properties on a consolidated basis, since their use and collection of data as described above will be the same across their different properties. To our knowledge, most of the hotel groups have completed at least one round of submissions at provincial CAC to create a record of ongoing compliance efforts.
A high-level system data flow chart is set out below:
How best to cooperate with law enforcement or inquiries?
Provincial CACs from time to time will carry out “enforcement sweeps” when unreported CBDT is suspected, whether due to guest reports or reports from privacy activists. If the provincial CAC approaches a property, the property team should report the case to the hotel group management (“above-property”) to ask them to explain to CAC the status of its security assessment. If no security assessment has yet been put in train, the above-property should accelerate the process and provide an estimate of when they will complete an initial submission to the CAC. Otherwise, there is a risk that the CAC will start enforcement. The CAC may then issue “rectification notices” (i.e. stipulating what actions they need to take in order to comply with the rules) to the hotel or hotel group if no evidence of CBDT compliance was found. We have seen a case (unrelated to hotels) where the targeted company was initially given less than one month to “rectify” its procedures, but such rectification period was eventually extended for another two months after negotiation.
FAQs
Question: What are the consequences of not reporting CBDT?
Answer: In our experience, if the hotel has been found not to have reported CBDT, the targeted company may request CAC to give it a chance and grace period to comply. However, there is no guarantee of lenience. If the company refuses to cooperate with CAC or put in place rectification measures, it may be subject to a fine. In our view, all hotels should cooperate. There is a hefty fine under PI Protection Law (PIPL) for illegal CBDT, which is up to RMB50 million or 5% of the company’s annual turnover. There is in process a draft Network Data Security Administration Regulation contemplating lowering the fine for illegal CBDT to RMB10million, but that rule remains a draft and is not finalized yet. Under the same draft rule, CAC has the power to stop data transmission if a company fails to report its CBDT activities. Solid work on data mapping, threshold analysis and evaluation reports are the first steps to kick off CBDT compliance improvement, which will help company explain and prove its compliance efforts to the regulator when being inspected.
Question: Who should report CBDT: property or above-property?
Answer: Above-property. As mentioned above, to save costs, international hotel groups can report CBDT on behalf of all of its participating properties on a consolidated basis. Added to that, in both management and franchise models, the above-property remains data controller for CRS, PMS and LMS systems and only licenses them to the owner to provide accommodation services.
Question: Is data localization required?
Answer: We should also mention data localization, which applies to CBDT by Critical Information Infrastructure Operators (CIIO) and imposes the most stringent CBDT legal control. Under a draft rule released by CAC in June 2016, known as National Cybersecurity Inspection Operating Guideline, if a 2C e-commerce platform has more than 10 million registered users, it is considered a CIIO. Although this draft rule has never been finalized, it is a de facto guide. Under the Personal Information Protection Law (“PIPL”), CIIOs must store data locally and conduct a security assessment before transferring data abroad. Consequently, certain leading international hotel groups and retail groups have already pre-emptively completed data localization. Hotel groups have not migrated their core systems, but have created local “first copy,” i.e., data will be saved in China first before being transferred abroad. A famous retail brand has completed “full stack localization”, where all systems, including the order processing system, has been localized.
Question: What CBDT is exempted from transfer mechanisms?
Answer: Small-scale general PI outbound transfers or a few specific scenarios (including where sensitive PI is involved) as listed in the New Rule are exempt from the Transfer Mechanisms. Specifically, transfers that involve less than 100,000 individuals’ general PI in a YTD period or those for purposes of booking overseas hotels, human resources management, etc., are exempted.
Question: What does an international hotel group need to do to pass security assessment?
Answer: In a security assessment, the CAC reviews the legality, the legitimacy and the necessity of a CBDT. Legality is a review if the hotel group has obtained proper consent from guests for the CBDT or there are other lawful bases. Legitimacy goes to whether the method of transfer matches with and is in proportion to the purpose of the transfer. Necessity covers if the data fields and the scale of the transfer are necessary to achieve the purpose of the transfer.
In our experience, the security assessment for international hotel groups has been an uphill battle for them because (a) few groups have built a robust notice-and-consent mechanism to collect guests’ separate consents for CBDT, (b) the CAC may view it unnecessary for domestic travel (i.e., a guest residing in Beijing booking a hotel in Shanghai) data to be processed by an overseas-based CRS system; and (c) the CAC may view it unnecessary for loyalty program data to be processed by an overseas-based LMS system.
With the recent relaxation of CBDT requirements, we see a trend for the CAC to ask if there is a business justification for the CBDT, for example, if the system needs to be supported by overseas-based staff, using overseas resources or otherwise has to be deployed outside of China to facilitate cross-border business. It’s possible that the CAC may one day allow an international hotel group to pass CBDT without localizing any of the core systems, but that situation has not arisen yet.
Question: What are the consequences of not passing security assessment?
Answer: If a company fails to pass the security assessment, it will be given a chance to put right (“rectify”) its CBDT scheme, for example, localizing certain systems and data, de-sensitizing certain data fields and re-filing the security assessment. We haven’t seen any cases where the CAC would order an immediate shut-down of business if security assessment has failed. However, the CAC may continue to follow up on the company’s rectification post-rejection to see if the company has implemented any rectification plan or if the company will re-submit for security assessment after localizing certain data fields for the rejected scenario but continuing to export others.
Question: How should I complete the CBDT Security Assessment and how long does it take?
Answer: Under the PIPL, CBDT is defined as a special data processing activity. Similar to GDPR, there is a concept of DPIA (data privacy impact assessment) under PIPL. The CBDT Security Assessment is essentially about a data controller running a DPIA on its CBDT and then submitting the result to the CAC for approval. It is worth noting that different implementing measures of the PIPL on CBDT provide specific requirements on the DPIA for CBDT which are more complex than the general DPIA requirement under the PIPL.
As such, the first step is a DPIA that starts with data mapping and threshold analysis, continues with identifying transfers/data flows in each business scenario, and finishes with identifying the risks and risk treatment.
Fangda assistance
In parallel with the DPIA, Fangda will work with international hotel groups to draft data transfer agreements in line with the CAC requirements, filling out the application forms and collecting and vetting other collaterals. After the DPIA is finished, Fangda will help to draft a self-assessment report and submit the report, along with other materials to the CAC for approval.
This self-assessment process roughly takes one to two months to complete.
After the application package is submitted, there will be a tabletop review by provincial CAC (for example, Shanghai CAC, Beijing CAC, etc.) which takes five business days to complete, followed by a substantial review by the central CAC in Beijing which takes 45 business days to complete.
Question: What are other international hotel companies doing?
Answer: Most international hotel groups operating in China are in the process of completing a security assessment for both topline business scenarios and backstage business scenarios. To our knowledge, most of the hotel groups have completed at least one round of submissions at provincial CAC to create a record. Some of the biggest chains have completed “first copy” data localization.
Question: What have been the impacts of the CBDT New Rule on international hotel companies?
Answer: Impacts of New Rule can best be described as both a tightening up and a relaxation. Compared to the draft of the New Rule that was released in September 2023, the finalized New Rule has “tightened up” regulation of sensitive PI, in the sense that there is no de minimis exemption for CBDT of sensitive PI – those below a 10,000-individual YTD volume threshold will be subject to standard contract filing/security certification, and above that threshold, security assessment. As such, almost all international hotel companies will be subject to security assessments.
That being said, the New Rule created certain scenario-based exemptions that benefit international hotel groups, as follows:
First and foremost is the “international travel” exemption, where if provision of PI is necessary for booking hotels, the underlying CBDT can be exempted from any Transfer Mechanism. We would caution that there are a few caveats to this exemption. First, the underlying contract must be a B2C contract where the guest is a contractual party – it doesn’t benefit B2B contract, such as MICE where business contact info will have to be provided cross-border to facilitate a booking. Second, in practice, the CAC may view it unnecessary for domestic travel (i.e., a guest residing in Beijing booking a hotel in Shanghai) data to be processed by an overseas-based CRS system.
The second is the HR exemption, where applicants will no longer need to disclose data transfer (including sensitive PI transfer) in HR management scenario in their security assessment. However, the HR exemption does not cover job applicant/candidate information, which will still need to be disclosed.